Governance that works in the Real World
Manual reviews are a hassle and easily skipped. Tenxity delivers eye-catching insights, spotlighting outliers to enhance your security oversight effortlessly
Whom we built for?
Security Teams
- Reduce manual effort by 80%
- With automated discovery and smart recommendations
- Identify critical risks faster
- Through visual anomaly detection and risk scoring
- Maintain continuous compliance
- With real-time monitoring and instant alerts
Compliance Officers
- Meet audit requirements effortlessly
- With automated documentation and reporting
- Demonstrate control effectiveness
- Through detailed certification trails and metrics
- Reduce compliance costs
- By streamlining review processes and reducing manual overhead

IT Managers
- Free up team resources
- From tedious manual reviews for strategic initiatives
- Improve accuracy
- By eliminating human error in access validation
- Scale governance programs
- Without proportional increases in staff or effort
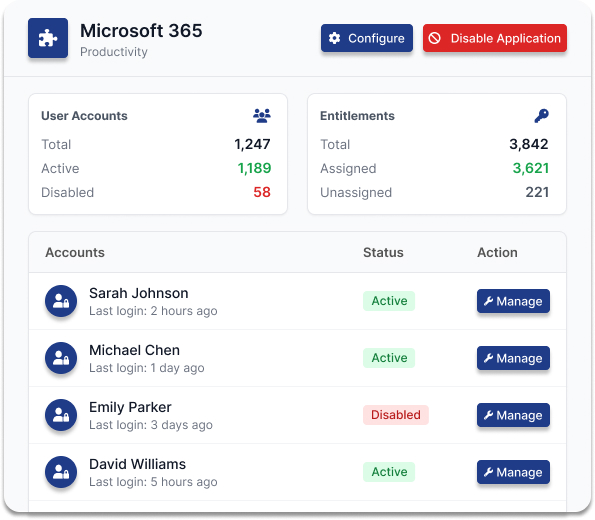
What makes tenxity governance different?
Intelligent Access Validation
Our smart engine automatically analyzes user permissions across all your systems, identifying high-risk access patterns and potential violations before they become problems.
Visual Anomaly Detection
Complex access relationships become clear through intuitive dashboards that highlight outliers, excessive permissions, and compliance risks at a glance.
Streamlined Certification Workflows
Automated workflows guide reviewers through efficient certification processes, with smart recommendations and bulk actions that reduce review time by 80%.
Continuous Compliance Monitoring
Real-time monitoring ensures access stays compliant between formal review cycles, with instant alerts for policy violations and unauthorised changes.
Core Features

Smart Risk Scoring
Advanced algorithms evaluate access risk based on user behavior, role requirements, and business context, prioritizing the reviews that matter most.

Cross-System Visibility
Unified view of user permissions across cloud platforms, enterprise applications, and on-premisessystems in a single, comprehensive dashboard.

Automate Recommendations
AI-powered suggestions for access modifications, role optimization, and policy improvements based on usage patterns and security best practices.

Audit-Ready Reports
Generate comprehensive compliance reports instantly, with detailed audit trails and certification documentation that satisfy regulators and auditors.
Get Started Today
Quick Setup
Deploy in weeks, not months, with pre-built connectors for major platforms and applications.
Seamless Integration
Works with your existing identity management infrastructure without requiring system changes.
Gradual Rollout
Start with high-risk areas and expand systematically, proving value at each phase.
Expert Support
Our governance specialists help optimize your program with best practices and ongoing guidance.

See Realtime Discovery in action with your own data
Start a Free Trial
